
.svg)
Portable bundle of media, manifests, provenance objects, and verification material.
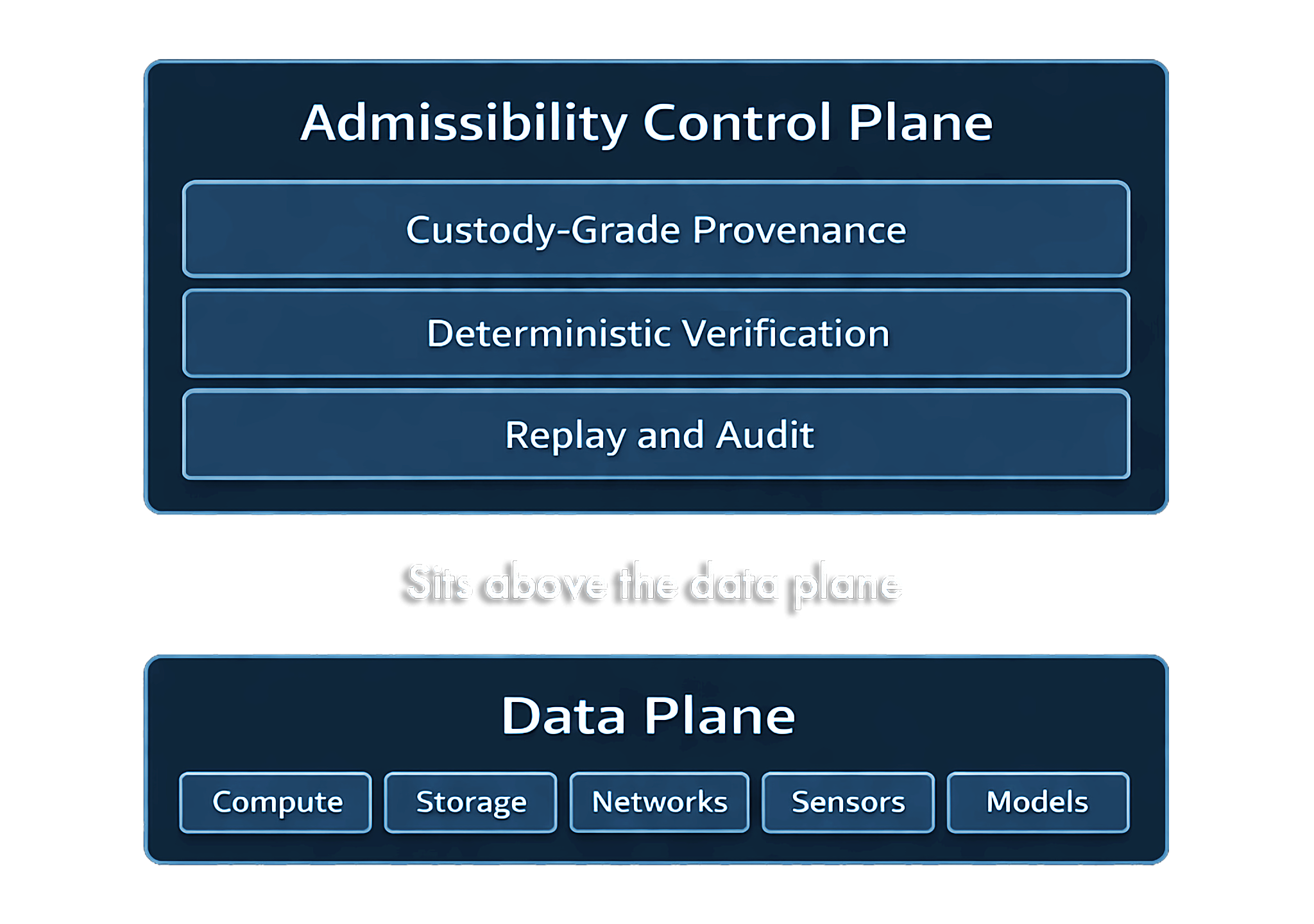
Third parties can validate packages without vendor systems or credentials.
Replay reconstructs the same timeline and boundaries across independent machines.
Every replay and export action is recorded in an integrity-protected ledger.
.png)